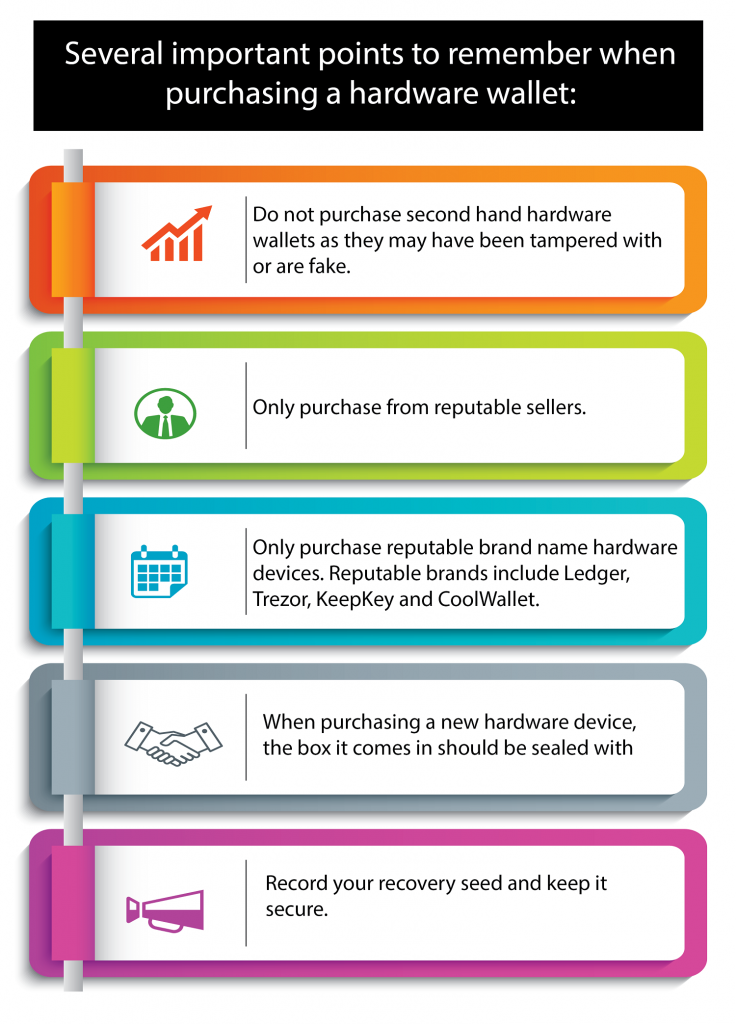
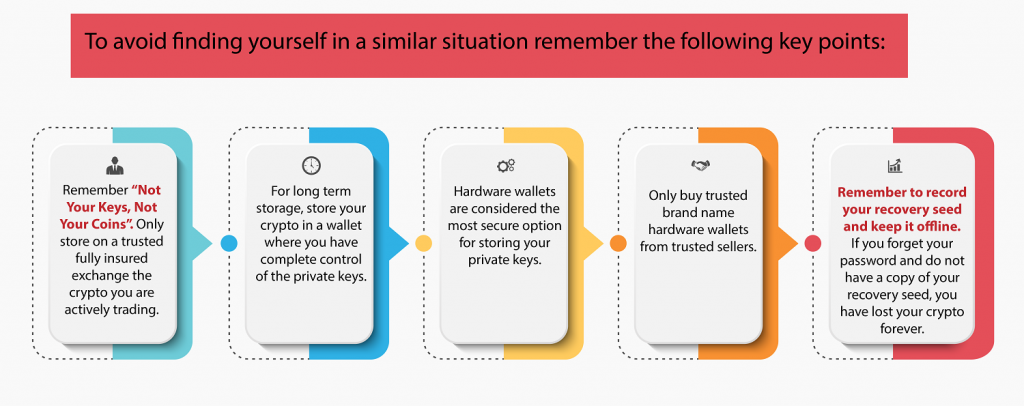
While cyber threats may not be in your control, your cyber security strategy is and you should be looking at a risk-based approach. This cyber security training course prepares managers and senior executives to understand, assess, and take a proactive approach in cyber security.
What you will learn from this course :
- Gain the knowledge of the threats faced by organizations and where they come from,
- what is required to create a Cyber Security Compliance Program,
- what is a Cyber Risk Assessment and why it is needed, how to rate your level of risk and how to perform a Cyber Risk Assessment.
- You will also cover what is a Cybersecurity Framework and what is required to prepare an Incident Response Plan.
- The course is a theory [Non-Technical]based course supported by group discussions and several exercises.
Who Should Attend:
Candidates should have a general awareness of information security and the need to respond to such events.
- Executives
- Incident managers
- IT managers
- Security officers
- Data Protection Officers (DPO)
- Manager – Compliance
Date & Time : Due to COVID this course is currently being run as an online course. Please contact us for further details.